AWS RDS Proxy: The Key to Flexibility, Security, and High Performance
🔄AWS RDS Proxy makes managing and scaling databases on Amazon RDS easier. It boosts performance, handles failovers smoothly, and simplifies database tasks. With connection pooling, it optimizes resource usage, ensuring efficient operations and better security.⚡️🔒
Table of contents
Use Cases
Flexible Traffic Redirection: Provides exceptional flexibility for redirecting and distributing database traffic to accommodate evolving application requirements. It enables seamless redirection of incoming traffic across multiple database instances without the need to modify application code.
Highly Scalable Database Connections: Simplifies managing database connections. With connection pooling and automatic scaling, it handles thousands of concurrent connections, ensuring scalability for your applications.
Improved Database Performance: By leveraging AWS RDS Proxy, you can enhance the performance of your applications that interact with the database. RDS Proxy helps reduce connection establishment times and handles connection pooling efficiently, resulting in faster response times and improved overall database performance.
Requirements
| Name | Version |
|---|---|
| Terraform | >= 1.0 |
| AWS CLI | >= 2.0 |
| OpenVPN | >= 2.5 |
Installation
Clone the repository
git clone https://github.com/BlackArrowGang/Arsenal.git
Go to the solution directory
cd /Arsenal/quiver/aws-rds-proxy
Install terraform modules
terraform init
Usage
Note: It might take a few minutes to fully create.
To use this code, follow these steps:
- Run the following commands
terraform plan
terraform apply
How It Works
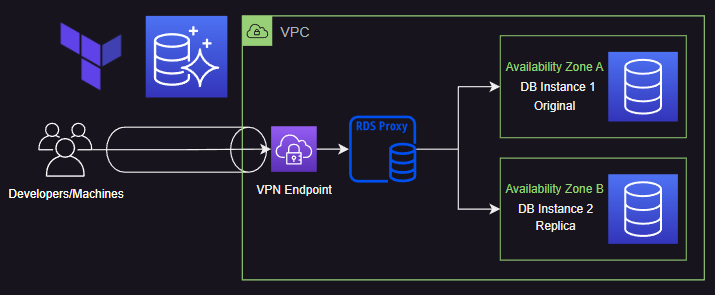
Provider and VPC Configuration:
- Configure the AWS provider with the default profile and region.
- Use the
terraform-aws-modules/vpc/awsmodule to create a VPC.- Specify the VPC name, availability zones, CIDR block, private subnets, and database subnets.
RDS Proxy Configuration:
- Use the
terraform-aws-modules/rds-proxy/awsmodule to create an RDS Proxy.- Specify the RDS Proxy name, IAM role name, and authentication mode.
- Create IAM policy and role if enabled.
- Configure VPC subnet IDs and security group IDs.
- Define RDS Proxy endpoints for read-write operations.
- Configure secrets for the RDS Proxy.
- Use the
RDS Aurora Configuration:
- Use the
terraform-aws-modules/rds-aurora/awsmodule to create an RDS Aurora cluster.- Specify the Aurora cluster name, engine, engine mode, and engine version.
- Set up the master username and password.
- Configure availability zones, instance class, and scaling configuration.
- Define VPC ID, database subnet group, and security group IDs.
- Set up security group rules, monitoring interval, encryption, and tags.
- Use the
Security Group Configuration:
Create a VPN access security group using the
terraform-aws-modules/security-group/awsmodule.- Specify the security group name, description, and VPC ID.
- Allow inbound traffic on UDP port 443 from any IP address.
Create an RDS access security group using the same module.
- Specify the security group name, description, and VPC ID.
- Allow inbound and outbound traffic on TCP port 5432 to and from itself.
Create a resource access security group using the same module.
- Specify the security group name, description, and VPC ID.
- Allow all inbound and outbound traffic to and from itself.
KMS Key Configuration:
- Use the
terraform-aws-modules/kms/awsmodule to create a KMS key.- Specify the key description and usage.
- Assign an alias to the KMS key.
- Use the
Secrets Configuration:
Create an AWS Secrets Manager secret for the RDS superuser credentials.
- Specify the secret name, description, and KMS key ID.
Create a secret version for the RDS superuser credentials.
- Associate the secret version with the previously created secret.
- Set the username and password for the RDS superuser.
Client VPN Configuration:
Create an AWS Client VPN endpoint.
- Specify the description, server certificate ARN, client CIDR block, split tunneling, VPC ID, and security group IDs.
- Configure certificate-based authentication with the root certificate chain ARN.
- Disable connection logging.
Authorize VPN access to the VPC.
- Associate the Client VPN endpoint with the VPC and allow access to all groups.
Associate subnets with the Client VPN endpoint.
- Associate the Client VPN endpoint with each private subnet in the VPC.
Support
If you encounter any issues or need assistance setting things up, Hire us and we can do it for you.
Want to try things for yourself?, checkout our github repository Arsenal.
To get started, you can visit our website blackarrowgang.com to explore our services and schedule a meeting with our team. We are committed to providing you with the necessary support and guidance.
Dont forget to checkout our youtube channel Black Arrow Gang, where we will showcase the functionality of this services in the future.
And if you are feeling generous you can go ahead and buy us a cup a coffee.
